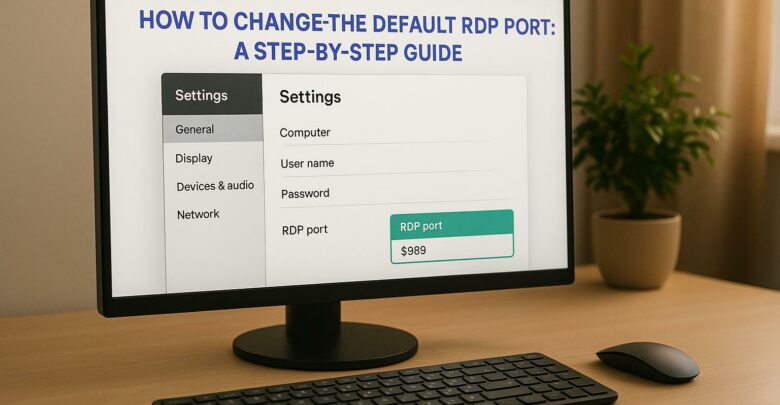
Learn how to change the default RDP port to enhance security and reduce exposure to attacks. Understand the limitations and necessary precautions.
Explore Windows 10/11 virtual desktops
Real-World Applications of flexidesktop

Cloud desktops can save SMBs money, boost security, and improve flexibility for remote work. They replace traditional PCs with virtual desktops hosted in the cloud, making IT easier to manage. Here’s a quick breakdown of what you need to know:
Pro Tip: Providers like flexidesktop offer plans starting at $19/month, tailored for SMB needs.
Before moving to cloud desktops, it’s essential to identify your IT challenges. For many SMBs, these include managing the costs of hardware lifecycles, supporting remote teams, and ensuring security across various devices.
Here’s what to assess:
To transition smoothly to cloud desktops, your technical setup must meet certain criteria. Evaluate these key components:
| Component | Assessment Criteria | Implementation Impact |
|---|---|---|
| Network | Location latency | Quality of user experience |
| Bandwidth | Connection speed | Number of concurrent users |
| End-user Devices | Hardware specifications | Compatibility with cloud tools |
| Applications | SaaS vs. on-premise ratio | Complexity of migration |
"It’s worth keeping in mind that in the cloud we’re all guinea pigs, and that means we’re all dispensable. Caveat cloudster." – Nick Carr, author of Does IT Matter?, The Big Switch and The Shallows [1]
Key steps for a successful assessment:
Once your technical readiness is confirmed, shift your focus to data governance and compliance.
After addressing technical needs, ensure your data storage and handling practices meet regulatory standards. Data governance plays a key role in implementing cloud desktops [3].
Regional Compliance Requirements:
"You need to be prepared to validate that independently. You can’t just rely on a set of generic documents." – Lee Sustar, Principal Analyst at Forrester [3]
Data Location Considerations:
Security is a top priority – 68% of business owners cite cybersecurity as a major concern [5]. When choosing a cloud desktop solution, focus on features that enhance efficiency and support business growth.
Here’s a breakdown of key features to evaluate:
| Feature Category | Requirements | Business Impact |
|---|---|---|
| Security | Multi-factor authentication, encryption, compliance tools | Protects data and ensures adherence to regulations |
| Performance | Dedicated CPU/RAM, storage options | Improves application speed and user productivity |
| Scalability | Simple resource adjustments, user management tools | Supports growth without disruptions |
| Backup Systems | Automated backups, disaster recovery options | Ensures business continuity during downtime |
| Support | 24/7 technical assistance, response time SLAs | Reduces downtime and keeps operations running smoothly |
A thorough cost analysis will help you avoid unexpected expenses [4]. When assessing cloud desktop services, take into account both direct and hidden costs.
Direct Costs:
Hidden Costs:
"Organizations that diligently match their computing power to the cloud use cases they support will be able to avoid overprovisioning compute or storage capacity." – Kevin Bogusch, Oracle Senior Competitive Analyst [6]
To budget effectively, calculate the Total Cost of Ownership (TCO). This should include monthly operational costs, setup and migration expenses, training, and projected growth over the next 12-24 months.
Once you’ve completed this analysis, consider how flexidesktop’s solutions align with these criteria.
flexidesktop specializes in cloud desktop solutions tailored for small to medium-sized businesses (SMBs). Plans start at $19 per month for basic setups and scale to advanced configurations with dedicated resources.
What flexidesktop Offers:
You can choose a plan based on your workload needs:
Each solution includes robust security features like private networks and VPN access, addressing SMBs’ cybersecurity challenges while ensuring smooth operations.
Start by evaluating your cloud desktops to identify critical data assets and potential vulnerabilities. Use the table below to guide your assessment:
| Security Domain | Key Considerations | Implementation Priority |
|---|---|---|
| Access Control | User authentication, session management, admin privileges | High – Address within the first week |
| Data Protection | Encryption needs, backup strategies, compliance standards | High – Configure before migration |
| Network Security | VPN setup, traffic monitoring, segmentation | Medium – Implement during deployment |
| Endpoint Protection | Antivirus, malware prevention, device management | Medium – Deploy alongside virtual desktops |
Once you’ve mapped out vulnerabilities, move quickly to establish strong security controls.
Follow these steps to enhance your security controls:
These security measures not only protect your cloud environment but also align with your migration strategy. To meet industry-specific requirements, conduct the following compliance checks:
To maintain compliance, implement these actions:
Schedule quarterly security reviews and provide annual training for employees to reinforce best practices.
Ongoing monitoring is key to maintaining security and compliance. Use the table below to guide your monitoring efforts:
| Monitoring Type | Frequency | Key Metrics |
|---|---|---|
| Access Logs | Daily | Failed login attempts, unusual access patterns |
| Security Events | Real-time | Malware detection, policy violations |
| Compliance Checks | Weekly | Policy adherence, certification status |
| User Activity | Continuous | Resource usage, data access patterns |
Before starting the migration, it’s critical to back up your data to avoid the risk of losing important information [8].
| Data Type | Recommended Frequency | Example Storage Options |
|---|---|---|
| User Profiles | Daily or as needed | Primary and secondary cloud storage |
| Business Documents | Multiple times per day | Encrypted cloud storage |
| Application Settings | Weekly or with updates | Secure cloud backup |
| System Configurations | Before migration | Dedicated backup server |
Your backup plan should align with your recovery goals and meet any compliance standards.
Once backups are in place, the next step is transferring user data and applications.
After completing the data transfer, test the system’s performance to ensure everything is functioning properly.
| Test Type | Key Metrics | Success Criteria |
|---|---|---|
| Network Performance | Latency, bandwidth usage | Meets performance targets with minimal delays |
| Application Response | Load time, functionality | Applications work reliably under normal usage |
| User Access | Login success, multi-factor checks | Users can log in securely and without issues |
| Data Integrity | File consistency, synchronization | Data is intact and fully synchronized |
Monitor system performance closely for the first 48 hours after migration. Set up automated alerts to quickly detect and address:
With data migration completed and initial tests confirming system stability, the next steps focus on final system validation, staff training, and setting up a reliable support system.
Evaluate cloud desktop performance systematically across different devices and scenarios:
| Test Category | Key Elements | Success Metrics |
|---|---|---|
| User Experience | Login process, app responsiveness | Response time under 2 seconds |
| Device Compatibility | Desktop, laptop, mobile access | Consistent performance across platforms |
| Network Stability | During peak hours | 99.9% uptime |
| Security Controls | Access permissions, data encryption | All security protocols verified |
During the first week, monitor performance during peak hours to identify any potential bottlenecks.
Training plays a crucial role in ensuring smooth adoption of cloud desktops. Research indicates that 95% of organizations see a lack of cloud-related skills as a key challenge [10].
| Training Phase | Duration | Focus Areas |
|---|---|---|
| Initial Orientation | 2–3 hours | Basic navigation and login |
| Core Features | 1 week | Daily tasks and file management |
| Advanced Functions | 2 weeks | Collaboration tools and security practices |
| Ongoing Support | Monthly | Updates and new features |
For instance, during the COVID-19 pandemic, Zapdesk successfully transitioned hundreds of office-based employees to remote work within 48 hours. This was largely thanks to their well-structured training program [11].
A well-trained team paired with a strong support system ensures minimal downtime and smooth operations. Considering that 40% of global SMBs lack in-house IT staff [10], having a robust support framework is crucial.
Key support components include:
To handle issues efficiently during and after the launch, implement the following support structure:
| Priority Level | Response Time | Resolution Target | Escalation Path |
|---|---|---|---|
| Critical | 15 minutes | 1 hour | Senior IT support |
| High | 30 minutes | 4 hours | System administrator |
| Medium | 2 hours | 8 hours | Technical support |
| Low | 4 hours | 24 hours | Help desk |
Use automated monitoring tools to identify issues before they affect users. Additionally, schedule weekly system health checks to maintain consistent performance.
Implementing cloud desktops successfully requires a focus on both technical details and business goals. With over 50% of SMBs’ technology budgets now allocated to cloud services [13], following a clear plan is essential.
| Implementation Phase | Key Requirements | Indicators of Success |
|---|---|---|
| Business Analysis | Network review and cost analysis | ROI metrics clearly defined |
| Security Setup | Firewall setup and endpoint security | All protocols fully verified |
| Data Migration | Backup checks and transfer testing | Transition completed without data loss |
| Launch Preparation | Staff training and support systems | 95% of users ready to go |
This framework outlines the main steps and ensures the process stays on track, setting the foundation for measurable business improvements.
Cloud desktops can streamline operations and cut costs. Research indicates businesses save 31% on costs by moving legacy applications to the cloud and reduce unplanned downtime by 69% [13].
Some of the key advantages for SMBs include:
To maintain success over time, it’s important to:
Experts emphasize that cloud migration isn’t just a tech upgrade – it’s a shift in how businesses operate and compete in the digital age. This change is essential for staying competitive and thriving in today’s fast-paced market.
While cloud desktops can offer significant benefits, SMBs should be aware of potential unexpected costs. These may include:
To avoid surprises, SMBs should carefully evaluate their provider’s pricing structure, monitor usage to optimize costs, and plan for any additional services that might be needed during or after implementation.
To ensure your network and devices are ready for cloud desktops, start by evaluating your network infrastructure. Check that your internet bandwidth and latency can handle the demands of virtual desktops, especially if multiple users will be accessing them simultaneously. A stable, high-speed connection is essential for smooth performance.
Next, review the devices your team plans to use. While cloud desktops typically work on a wide range of devices, including older hardware, ensure they meet the minimum specifications recommended by your provider. This helps guarantee compatibility and a seamless user experience.
If you’re unsure about your setup, consider consulting with your cloud desktop provider or IT advisor to identify any gaps and optimize your environment for a successful implementation.
When transitioning to cloud desktops, prioritizing security is essential to protect your business data. Start by enabling multi-factor authentication (MFA) to add an extra layer of protection. Ensure that all data, both at rest and in transit, is secured with strong encryption. Limit user access with least privilege principles, allowing employees only the permissions they need.
Regularly update and patch software to address vulnerabilities, and implement security monitoring tools to detect and prevent potential threats. Additionally, establish a data backup and recovery plan to ensure business continuity in case of incidents. Finally, choose a reliable cloud provider with a proven track record in security and compliance.
By following these steps, you can create a secure and resilient environment for your cloud desktops, safeguarding your sensitive business information effectively.

Learn how to change the default RDP port to enhance security and reduce exposure to attacks. Understand the limitations and necessary precautions.

Learn how to enable multiple user sessions on a single device using a managed solution that simulates a Windows 11 experience.

Explore how GPU-accelerated virtual desktops are revolutionizing architecture firms by enhancing collaboration, reducing costs, and improving rendering efficiency.

Explore the differences between remote desktops and virtual desktops, their pros and cons, and which solution best suits your business needs.

Learn how cloud latency is affected by data center location, compliance laws, and infrastructure, and discover strategies to enhance performance.

Launch your startup without hefty hardware costs using virtual desktops for flexibility, scalability, and enhanced security.

Virtual desktops are essential for small businesses in 2025, reducing costs, enhancing security, and supporting remote work flexibility.

Learn essential strategies to protect sensitive data during cloud migration, ensuring compliance and minimizing security risks.

Explore the differences between on-premises and hybrid VDI, examining their costs, scalability, and security to find the best fit for your business needs.

